Did You Know…..
Posted By thestatedtruth.com on December 17, 2010
Posted By thestatedtruth.com on December 17, 2010
Posted By thestatedtruth.com on December 17, 2010
Liar Liar Pants On Fire! The chart below is total consumer credit outstanding. Interestingly, when we looked at it, somehow it showed an uptick. That seemed odd and didn’t square with the credit card data. Low and behold…… they (the government) now count student loans as consumer credit, whereas they did not in the past. Geez, so federally supported credit (ie. student-backed loans) accounted for all the increase last month a record $31.8 billion expansion. Actually, the unadjusted data shows a $700 million decline! Hmm……so over the past three months consumer credit outstanding net of federal student assisted loans actually has collapsed $76 billion ….. this degree of contraction is without precedent.”

David Rosenberg, who looked a little deeper into the data says that they now count student loans as consumer credit, whereas they did not in the past. This from David:
“Is The Credit Contraction Over?
“What do you know? Outstanding U.S. consumer credit expanded $3.3 billion in October after eking out a $1.3 billion increase in September. This is the first back-to back gain since just before Hank Paulson took out his bazooka in the summer of 2008.
“Does this mean the credit contraction is over? No.
“First, the raw not seasonally adjusted data shows a $700 million decline. Once again, it was federally supported credit (ie. student-backed loans) that accounted for all the increase last month a record $31.8 billion expansion. Commercial banks, securitized pools and finance companies posted huge declines to the point where excluding federal loans, consumer credit plunged $32.5 billion, to the lowest level since November 2004 (not to mention down a record 9% YoY). Over the past three months consumer credit outstanding net of federal student assisted loans has collapsed $76 billion … this degree of contraction is without precedent.”
Parts of this article quote John Mauldin of Millennium Wave Advisors
Posted By thestatedtruth.com on December 17, 2010
Debit cards are the new growth area…..”The lowest percentage of shoppers in the 27-year-history of a national survey said they used credit cards over the Thanksgiving weekend, while the use of general credit cards like Visa and MasterCard fell 11 percent in the third quarter from a year earlier, according to the credit bureau TransUnion.
“Britt Beemer, chief executive of America’s Research Group, a survey firm, said ‘The consumer really feels a lot of pressure from previous debts, and they just aren’t going to dig themselves into that kind of hole,’ he said.
“After the Thanksgiving shopping weekend, the group found that just about 17 percent were paying with credit … just over half of last year’s level and the lowest rate in the 27 years it has conducted a survey.”
Credit lines have been reduced and cards have gone away. Debit cards are the current growth area, but such a drop-off in credit card debt is unprecedented, and the NYT-cited survey give no indications that it’s going to change soon.
Posted By thestatedtruth.com on December 17, 2010
Parts of this article were from www.thewallstreetjournal.com
Posted By thestatedtruth.com on December 16, 2010
The U.S. Congress passed an $858 billion bill extending for two years all Bush-era tax cuts, and now the measure goes to President Barack Obama for his signature.
Majorities of both parties supported the bill. Voting in favor were 139 Democrats and 138 Republicans, while 112 Democrats and 36 Republicans voted against it. Eight lawmakers didn’t vote.
The tax-cut plan extends through 2012 all Bush-era tax reductions on income, capital gains and dividends. It continues expanded unemployment insurance benefits through 2011, cuts payroll taxes by 2 percentage points during 2011 and lets businesses write off 100 percent of capital investments between Sept. 9, 2010, and Dec. 31, 2011. Obama agreed on the plan with Republicans on Dec. 6. The legislation also extends dozens of expired and expiring tax breaks, including a research and development tax credit and a college tuition tax credit that was created in last year’s economic stimulus law.
Under the plan negotiated with Obama, the estate tax next year would have a top rate of 35 percent to be applied after an exemption of $5 million per person.
Posted By thestatedtruth.com on December 16, 2010
Neal Soss at Credit Suisse:
We have rising prices in gasoline and food. That is worldwide. It is also the warning sign of the worst-case “nightmare scenario.â€Â It as an “eruption of headline inflation (food and gasoline) with no accompanying pick-up in wages or real growth.â€Â
David R. Kotok of Cumberland Advisors:
Through the December 10 data, foreigners have not been buyers of U.S. Treasury and agency debt. The home mortgage rate in the U.S. has backed up to nearly 5%. U.S. bond markets exhibit signs of panic selling. The Fed’s policy of U.S. Treasury purchases appears to be defeated by the markets. That suggests a possible economic weakening is coming in the spring and another downturn leg in housing is possible. Spain is now paying a real interest rate of 5% to borrow, according to its latest auction. The Eurozone issues are not resolved.
Posted By thestatedtruth.com on December 16, 2010
Let’s just say this is courtesy of the Wikileaks firestorm…
Did you know that E-mails are now today’s primary mode of communication (that’s the main reason the U.S. Post Office is basically broke) , and that e-mail has been subject to the same amount of government surveillance as having a phone bugged since the Patriot Act. Fair to assume this may force the Obama administration to do some drastic changes to its eavesdropping infrastructure and or the constitution.
The Electronic Frontier Foundation has a summary on this increasingly more critical issue:
In a landmark decision issued today in the criminal appeal of U.S. v. Warshak, the Sixth Circuit Court of Appeals has ruled that the government must have a search warrant before it can secretly seize and search emails stored by email service providers. Closely tracking arguments made by EFF in its amicus brief, the court found that email users have the same reasonable expectation of privacy in their stored email as they do in their phone calls and postal mail.
EFF filed a similar amicus brief with the 6th Circuit in 2006 in a civil suit brought by criminal defendant Warshak against the government for its warrantless seizure of his emails. There, the 6th Circuit agreed with EFF that email users have a Fourth Amendment-protected expectation of privacy in the email they store with their email providers, though that decision was later vacated on procedural grounds. Warshak’s appeal of his criminal conviction has brought the issue back to the Sixth Circuit, and once again the court has agreed with EFF and held that email users have a Fourth Amendment-protected reasonable expectation of privacy in the contents of their email accounts.
ÂAs the Court held today,
Given the fundamental similarities between email and traditional forms of communication [like postal mail and telephone calls], it would defy common sense to afford emails lesser Fourth Amendment protection…. It follows that email requires strong protection under the Fourth Amendment; otherwise the Fourth Amendment would prove an ineffective guardian of private communication, an essential purpose it has long been recognized to serve…. [T]he police may not storm the post office and intercept a letter, and they are likewise forbidden from using the phone system to make a clandestine recording of a telephone call–unless they get a warrant, that is. It only stands to reason that, if government agents compel an ISP to surrender the contents of a subscriber’s emails, those agents have thereby conducted a Fourth Amendment search, which necessitates compliance with the warrant requirement….
Posted By thestatedtruth.com on December 16, 2010
The most recent look at the 30 Year Cash Fannie Mortgage showed a rise by 11 bps overnight, and by a stunning 1% in the last month. At 4.703% the prevailing wholesale mortgage rate is back to the highest it has been since May 2010. And while some have speculated that this inflection in rates would have been sufficient to get Americans to jump on the band wagon refinancing their mortgages by attempting to catch low rates while they can, the jump has been so powerful that the refi’s got passed by this time.  As a result, ceteris paribus, home prices may have to decline by about 10% to compensate for the pick up in rates in just the last month.
Posted By thestatedtruth.com on December 16, 2010
WikiLeaks founder Julian Assange had his bail ruling in Britain upheld on appeal.  It was considered a setback to U.K. prosecutors who sought to keep him jailed during an extradition fight with Sweden.
The ruling today by the High Court in London upholds a Dec. 14 decision to free Assange on condition that he turn in his passport, wear an electronic tag and have an overnight curfew at a friend’s home. Assange must also post bail of 200,000 pounds ($311,800).
Posted By thestatedtruth.com on December 15, 2010
This chart sure goes back a long ways in time!  1792-Present!  Geez
Posted By thestatedtruth.com on December 15, 2010
When was the last time we saw this chart turn down…..Umm, You’re right if you said we haven’t….Until now!
Posted By thestatedtruth.com on December 15, 2010
ICI has just released money flows…..and we have the 32nd consecutive outflow from domestic equity mutual funds. Total outflows for the year to date are $96 billion.   We also saw for the first time in a while, an outflow of $401 million in taxable bond funds  (and $1.3 billion in outflows from muni bonds).
And here is the cumulative flows chart:
Posted By thestatedtruth.com on December 15, 2010
Wow! We’re not sure just where the President is going with this…….
The Hill reports that the president has been telling members of Congress that failure to pass the tax-cut legislation could result in the end of his presidency. This begs the question: How does one view this….Reuters reports 2010 may be the second highest bonus payout season on Wall Street…. ever!   Whether Obama’s departure would even be considered ‘bad thing’ at this point…well, that’s a deep subject no pun intended!
Posted By thestatedtruth.com on December 15, 2010
The U.S. Senate on Wednesday officially approved an $858 billion bill extending the Bush-era tax cuts for two years in an 81-19 vote. Next up the House vote…..huff and puff maybe as soon as Thursday.
The new legislation would extend Bush-era tax cuts for an additional two years for people of all income levels. It would cut payroll taxes for workers in 2011 and extend a range of expired business-tax breaks like the research-and-development credit. the legislation also reduces federal payroll taxes for most American workers for one year by two percentage points to 4.2% from 6.2%. Jobless benefits would be extended for 13 months as well as tax benefits Obama championed for low-income families that were part of 2009 economic-stimulus legislation.
The bill also allows businesses to write off 100% of equipment purchases made after Sept. 8, 2010, but before Jan. 1, 2012. It shields most taxpayers from the alternative minimum tax in 2010 and 2011. And it renews a host of expired tax breaks for businesses, including a tax break on banks’ overseas income, quicker depreciation for restaurant improvements and the 45-cent tax credit for ethanol blenders.
Posted By thestatedtruth.com on December 15, 2010
Looks like we’re seeing inflation but not the kind Ben Bernanke is trying to create, such as real estate going up, instead it’s commodities. Sugar at 30 year highs….stay tuned, many commodities (wheat, corn, soybeans,  rice etc.) may be getting ready to explode if any kind of shortages show up.
Portugal Tries to Prevent Sugar Hoarding Amid Shortage
By Alan Purkiss – Dec 14, 2010
Portugal faces a sugar shortage, the first European country to find itself in this position in more than three decades, the Financial Times reported.
Agriculture Minister Antonio Serrano asked people not to hoard the commodity after a breakdown in imports to refineries led to a run on supplies in the shops, the newspaper said.
Global sugar prices have reached a 30-year high.
Posted By thestatedtruth.com on December 15, 2010
Protesters: Â “We want the government to take back the latest labor law that will hurt workers’ rights.”….Not a chance, didn’t they hear that Greece is broke.
ATHENS, Greece (AP) — Protesters clashed with riot police across Athens on Wednesday, torching cars, hurling gasoline bombs and sending Christmas shoppers fleeing in panic during a general strike against the government’s latest austerity measures.
Police fired tear gas and flash grenades as the violence escalated outside parliament and spread to other parts of the capital.
Angry unions triggered the 24-hour strike to protest new labor reforms and pay cuts as Greece struggles to reshape its economy under conditions set by a euro110 billion ($146 billion) international bailout. The strike also grounded flights, closed factories, disrupted hospitals and shut down trains, ferries and buses across the country.
It was the seventh strike this year by unions appalled at a wave of austerity policies meant to pull Greece out of its worst financial crisis since World War II.
“There is huge participation in this strike … I believe it will put pressure on the government,” Stathis Anestis, deputy leader of Greece’s largest union, the GSEE, told The Associated Press. “We want the government to take back the latest labor law that will hurt workers’ rights.”
More at: http://finance.yahoo.com/news/Antiausterity-riots-erupt-apf-3130705059.html?x=0&.v=5
Posted By thestatedtruth.com on December 14, 2010
A lawyer for Julian Assange of WikiLeaks says a secret grand jury is meeting outside Washington to consider charges in the release of thousands of sensitive U.S. documents.
Mark Stephens, one of Wikileaks lawyers told David Frost on Al-Jazeera television that they have heard from Swedish authorities that there has been a “secretly empaneled” grand jury in Alexandria, Virginia.
Posted By thestatedtruth.com on December 14, 2010
By George Friedman
Julian Assange has declared that geopolitics will be separated into pre-“Cablegate†and post-“Cablegate†eras. That was a bold claim. However, given the intense interest that the leaks produced, it is a claim that ought to be carefully considered. Several weeks have passed since the first of the diplomatic cables were released, and it is time now to address the following questions: First, how significant were the leaks? Second, how could they have happened? Third, was their release a crime? Fourth, what were their consequences? Finally, and most important, is the WikiLeaks premise that releasing government secrets is a healthy and appropriate act a tenable position?
Let’s begin by recalling that the U.S. State Department documents constituted the third wave of leaks. The first two consisted of battlefield reports from Iraq and Afghanistan. Looking back on those as a benchmark, it is difficult to argue that they revealed information that ran counter to informed opinion. I use the term “informed opinion†deliberately. For someone who was watching Iraq and Afghanistan with some care over the previous years, the leaks might have provided interesting details but they would not have provided any startling distinction between the reality that was known and what was revealed. If, on the other hand, you weren’t paying close attention, and WikiLeaks provided your first and only view of the battlefields in any detail, you might have been surprised.
Let’s consider the most controversial revelation, one of the tens of thousands of reports released on Iraq and Afghanistan and one in which a video indicated that civilians were deliberately targeted by U.S. troops. The first point, of course, is that the insurgents, in violation of the 1949 Geneva Conventions, did not go into combat wearing armbands or other distinctive clothing to distinguish themselves from non-combatants. The Geneva Conventions have always been adamant on this requirement because they regarded combatants operating under the cover of civilians as being responsible for putting those civilians in harm’s way, not the uniformed troops who were forced to distinguish between combatants and non-combatants when the combatants deliberately chose to act in violation of the Geneva Conventions.
It follows from this that such actions against civilians are inevitable in the kind of war Iraqi insurgents chose to wage. Obviously, this particular event has to be carefully analyzed, but in a war in which combatants blend with non-combatants, civilian casualties will occur, and so will criminal actions by uniformed troops. Hundreds of thousands of troops have fought in Iraq, and the idea that criminal acts would be absent is absurd. What is most startling is not the presence of potentially criminal actions but their scarcity. Anyone who has been close to combat or who has read histories of World War II would be struck not by the presence of war crimes but by the fact that in all the WikiLeaks files so few potential cases are found. War is controlled violence, and when controls fail — as they inevitably do — uncontrolled and potentially criminal violence occurs. However, the case cited by WikiLeaks with much fanfare did not clearly show criminal actions on the part of American troops as much as it did the consequences of the insurgents violating the Geneva Conventions.
Only those who were not paying attention to the fact that there was a war going on, or who had no understanding of war, or who wanted to pretend to be shocked for political reasons, missed two crucial points: It was the insurgents who would be held responsible for criminal acts under the Geneva Conventions for posing as non-combatants, and there were extraordinarily few cases of potential war crimes that were contained in the leaks.
The diplomatic leaks are similar. There is precious little that was revealed that was unknown to the informed observer. For example, anyone reading STRATFOR knows we have argued that it was not only the Israelis but also the Saudis that were most concerned about Iranian power and most insistent that the United States do something about it. While the media treated this as a significant revelation, it required a profound lack of understanding of the geopolitics of the Persian Gulf to regard U.S. diplomatic cables on the subject as surprising.
U.S. Defense Secretary Robert Gates’ statement in the leaks that the Saudis were always prepared to fight to the last American was embarrassing, in the sense that Gates would have to meet with Saudi leaders in the future and would do so with them knowing what he thinks of them. Of course, the Saudis are canny politicians and diplomats and they already knew how the American leadership regarded their demands.
There were other embarrassments also known by the informed observer. Almost anyone who worries about such things is aware that Italian Prime Minister Silvio Berlusconi is close to the Russians and likes to party with young women. The latest batch of leaks revealed that the American diplomatic service was also aware of this. And now Berlusconi is aware that they know of these things, which will make it hard for diplomats to pretend that they don’t know of these things. Of course, Berlusconi was aware that everyone knew of these things and clearly didn’t care, since the charges were all over Italian media.
I am not cherry-picking the Saudi or Italian memos. The consistent reality of the leaks is that they do not reveal anything new to the informed but do provide some amusement over certain comments, such as Russian Prime Minister Vladimir Putin and President Dmitri Medvedev being called “Batman and Robin.†That’s amusing, but it isn’t significant. Amusing and interesting but almost never significant is what I come away with having read through all three waves of leaks.
Obviously, the leaks are being used by foreign politicians to their own advantage. For example, the Russians feigned shock that NATO would be reassuring the Balts about defense against a potential Russian invasion or the Poles using the leaks to claim that solid U.S.-Polish relations are an illusion. The Russians know well of NATO plans for defending the Baltic states against a hypothetical Russian invasion, and the Poles know equally well that U.S.-Polish relations are complex but far from illusory. The leaks provide an opportunity for feigning shock and anger and extracting possible minor concessions or controlling atmospherics. They do not, however, change the structure of geopolitics.
Indeed, U.S. diplomats come away looking sharp, insightful and decent. While their public statements after a conference may be vacuous, it is encouraging to see that their read of the situation and of foreign leaders is unsentimental and astute. Everything from memos on senior leaders to anonymous snippets from apparently junior diplomats not only are on target (in the sense that STRATFOR agrees with them) but are also well-written and clear. I would argue that the leaks paint a flattering picture overall of the intellect of U.S. officials without revealing, for the most part, anything particularly embarrassing.
At the same time, there were snarky and foolish remarks in some of the leaks, particularly personal comments about leaders and sometimes their families that were unnecessarily offensive. Some of these will damage diplomatic careers, most generated a good deal of personal tension and none of their authors will likely return to the countries in which they served. Much was indeed unprofessional, but the task of a diplomat is to provide a sense of place in its smallest details, and none expect their observations ever to be seen by the wrong people. Nor do nations ever shift geopolitical course over such insults, not in the long run. These personal insults were by far the most significant embarrassments to be found in the latest release. Personal tension is not, however, international tension.
This raises the question of why diplomats can’t always simply state their minds rather than publicly mouth preposterous platitudes. It could be as simple as this: My son was a terrible pianist. He completely lacked talent. After his recitals at age 10, I would pretend to be enthralled. He knew he was awful and he knew I knew he was awful, but it was appropriate that I not admit what I knew. It is called politeness and sometimes affection. There is rarely affection among nations, but politeness calls for behaving differently when a person is in the company of certain other people than when that person is with colleagues talking about those people. This is the simplest of human rules. Not admitting what you know about others is the foundation of civilization. The same is true among diplomats and nations.
And in the end, this is all I found in the latest WikiLeaks release: a great deal of information about people who aren’t American that others certainly knew and were aware that the Americans knew, and now they have all seen it in writing. It would take someone who truly doesn’t understand how geopolitics really works to think that this would make a difference. Some diplomats may wind up in other postings, and perhaps some careers will be ended. But the idea that this would somehow change the geopolitics of our time is really hard to fathom. I have yet to see Assange point to something so significant that it would justify his claim. It may well be that the United States is hiding secrets that would reveal it to be monstrous. If so, it is not to be found in what has been released so far.
There is, of course, the question of whether states should hold secrets, which is at the root of the WikiLeaks issue. Assange claims that by revealing these secrets WikiLeaks is doing a service. His ultimate maxim, as he has said on several occasions, is that if money and resources are being spent on keeping something secret, then the reasons must be insidious. Nations have secrets for many reasons, from protecting a military or intelligence advantage to seeking some advantage in negotiations to, at times, hiding nefarious plans. But it is difficult to imagine a state — or a business or a church — acting without confidentiality. Imagine that everything you wrote and said in an attempt to figure out a problem was made public? Every stupid idea that you discarded or clueless comment you expressed would now be pinned on you. But more than that, when you argue that nations should engage in diplomacy rather than war, taking away privacy makes diplomacy impossible. If what you really think of the guy on the other side of the table is made public, how can diplomacy work?
This is the contradiction at the heart of the WikiLeaks project. Given what I have read Assange saying, he seems to me to be an opponent of war and a supporter of peace. Yet what he did in leaking these documents, if the leaking did anything at all, is make diplomacy more difficult. It is not that it will lead to war by any means; it is simply that one cannot advocate negotiations and then demand that negotiators be denied confidentiality in which to conduct their negotiations. No business could do that, nor could any other institution. Note how vigorously WikiLeaks hides the inner workings of its own organization, from how it is funded to the people it employs.
Assange’s claims are made even more interesting in terms of his “thermonuclear†threat. Apparently there are massive files that will be revealed if any harm comes to him. Implicit is the idea that they will not be revealed if he is unharmed — otherwise the threat makes no sense. So, Assange’s position is that he has secrets and will keep them secret if he is not harmed. I regard this as a perfectly reasonable and plausible position. One of the best uses for secrets is to control what the other side does to you. So Assange is absolutely committed to revealing the truth unless it serves his interests not to, in which case the public has no need to know.
It is difficult to see what harm the leaks have done, beyond embarrassment. It is also difficult to understand why WikiLeaks thinks it has changed history or why Assange lacks a sufficient sense of irony not to see the contradiction between his position on openness and his willingness to keep secrets when they benefit him. But there is also something important here, which is how this all was leaked in the first place.
To begin that explanation, we have to go back to 9/11 and the feeling in its aftermath that the failure of various government entities to share information contributed to the disaster. The answer was to share information so that intelligence analysts could draw intelligence from all sources in order to connect the dots. Intelligence organizations hate sharing information because it makes vast amounts of information vulnerable. Compartmentalization makes it hard to connect dots, but it also makes it harder to have a WikiLeaks release. The tension between intelligence and security is eternal, and there will never be a clear solution.
The real issue is who had access to this mass of files and what controls were put on them. Did the IT department track all external drives or e-mails? One of the reasons to be casual is that this was information that was classified secret and below, with the vast majority being at the confidential, no-foreign-distribution level. This information was not considered highly sensitive by the U.S. government. Based on the latest trove, it is hard to figure out how the U.S. government decides to classify material. But it has to be remembered that given their level of classification these files did not have the highest security around them because they were not seen as highly sensitive.
Still, a crime occurred. According to the case of Daniel Ellsberg, who gave a copy of the Pentagon Papers on Vietnam to a New York Times reporter, it is a crime for someone with a security clearance to provide classified material for publication but not a crime for a publisher to publish it, or so it has become practice since the Ellsberg case. Legal experts can debate the nuances, but this has been the practice for almost 40 years. The bright line is whether the publisher in any way encouraged or participated in either the theft of the information or in having it passed on to him. In the Ellsberg case, he handed it to reporters without them even knowing what it was. Assange has been insisting that he was the passive recipient of information that he had nothing to do with securing.
Now it is interesting whether the sheer existence of WikiLeaks constituted encouragement or conspiracy with anyone willing to pass on classified information to him. But more interesting by far is the sequence of events that led a U.S. Army private first class not only to secure the material but to know where to send it and how to get it there. If Pfc. Bradley Manning conceived and executed the theft by himself, and gave the information to WikiLeaks unprompted, Assange is clear. But anyone who assisted Manning or encouraged him is probably guilty of conspiracy, and if Assange knew what was being done, he is probably guilty, too. There was talk about some people at MIT helping Manning. Unscrambling the sequence is what the Justice Department is undoubtedly doing now. Assange cannot be guilty of treason, since he isn’t a U.S. citizen. But he could be guilty of espionage. His best defense will be that he can’t be guilty of espionage because the material that was stolen was so trivial.
I have no idea whether or when he got involved in the acquisition of the material. I do know — given the material leaked so far — that there is little beyond minor embarrassments contained within it. Therefore, Assange’s claim that geopolitics has changed is as false as it is bold. Whether he committed any crime, including rape, is something I have no idea about. What he is clearly guilty of is hyperbole. But contrary to what he intended, he did do a service to the United States. New controls will be placed on the kind of low-grade material he published. Secretary of Defense Gates made the following point on this:
“Now, I’ve heard the impact of these releases on our foreign policy described as a meltdown, as a game-changer, and so on. I think those descriptions are fairly significantly overwrought. The fact is, governments deal with the United States because it’s in their interest, not because they like us, not because they trust us, and not because they believe we can keep secrets. Many governments — some governments — deal with us because they fear us, some because they respect us, most because they need us. We are still essentially, as has been said before, the indispensable nation.
“Is this embarrassing? Yes. Is it awkward? Yes. Consequences for U.S. foreign policy? I think fairly modest.â€
I don’t like to give anyone else the final word, but in this case Robert Gates’ view is definitive. One can pretend that WikiLeaks has redefined geopolitics, but it hasn’t come close.
Simply copy and paste this code:
Posted By thestatedtruth.com on December 14, 2010
A judge in the U.K. granted WikiLeaks founder Julian Assange bail but he fights sexual-misconduct accusations in Sweden and will remain in custody after Swedish prosecutors said they would challenge the decision.
Posted By thestatedtruth.com on December 13, 2010
The blizzard that pummeled the Upper Midwest over the weekend was one for the record books, burying some communities with nearly 2 feet of snow and breaking 100-year-old records in others and all the way to the South, new records have been set as snow and brutally cold air blasted in behind the storm.
Minnesota and Wisconsin were hardest-hit by the blizzard, with more than 20 inches of snow piling up east of the Twin Cities and into western parts of Wisconsin Friday night into Saturday night.
Snowfall totals reached 23.0 inches near Osceola, Wis., 22.0 inches in Eau Claire, Wis., and 21.5 inches in New Market and Shakopee, Minn.

This image shows snow depth across the country as of Monday, Dec. 13, 2010. The snowstorm over the weekend significantly increased the percentage of snow cover for the contiguous U.S., as it dropped measurable snow in the central Plains and the mid-Mississippi and Tennessee valleys.
The 17.1 inches that fell in Minneapolis from Dec. 10-11 set the all-time record for two-day snowfall in December.
Posted By thestatedtruth.com on December 13, 2010
This added interest expense should bust state and local budgets for next year. So what’s a borrower to do? Well to start…cut backs are in order across the board and that’s official!
Investors are demanding higher interest payments on municipal bonds in a race for year-end issuance.  Yields are pushing highest rates since 2009 while the Build America Bonds program appeared increasingly unlikely to be extended.
The purpose of Build America Bonds is to reduce the cost of borrowing for state and local government issuers and governmental agencies. Build America Bonds are taxable municipal bonds that carry special tax credits and federal subsidies for either the bond issuer or the bondholder. Build America Bonds were created under Section 1531 of Title I of Division B of the American Recovery and Reinvestment Act that U.S. President Barack Obama signed into law on February 17, 2009.
Posted By thestatedtruth.com on December 13, 2010
The $858+ billion bill to extend the Bush tax cuts has secured 60 votes in the Senate, the minimum needed to schedule a final vote. That tally effectively gives a green-light for the Senate to finish the debate and send the package to the House. Inquiring minds wonder what kind of pork was added to this monstrosity.
Posted By thestatedtruth.com on December 13, 2010
Goldman Sachs Predicts Best Commodity Returns for 2011 will be in Precious Metals….. The raw materials most affected for 2011 will be those with the tightest supply, including crude oil, copper, cotton, soybeans and platinum….and we think you might want to add wheat, corn and rice to that list!
By Maria Kolesnikova – Dec 13, 2010
Precious metals will probably give investors the best returns among commodities in the next year, and livestock the worst, Goldman Sachs Group Inc. said.
Precious metals will advance 28 percent over 12 months and livestock 4 percent, London-based Jeffrey Currie, Allison Nathan and other Goldman analysts said in a report today. The team raised its 12-month forecast for the S&P GSCI Enhanced Total Return Index to 18 percent from 16 percent, mostly because of changes to agricultural estimates.
“Extreme weakness in U.S. demand over the past two years has allowed China to grow unconstrained without any competition for raw materials,†the Goldman analysts said in the report. “This is likely to change in 2011 with a stronger U.S. that is likely to bump up against a China that is consuming dramatically more commodities than pre-crisis.â€
Posted By thestatedtruth.com on December 12, 2010
As this chart from Calculated Risk shows we’re about 99 weeks since the very worst of the job losses from late-2008/early-2009. The extent to which their cutoff effects the consumer recovery (and thus everything else) is something to consider.
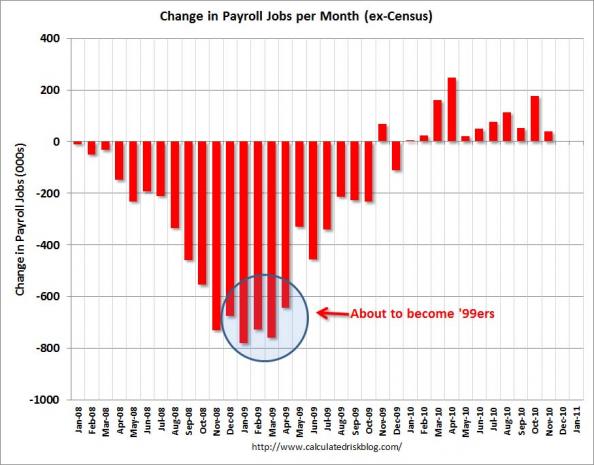
Read more: www.businessinsider.com
Posted By thestatedtruth.com on December 12, 2010
No good solutions ahead and problems galore, but this one was needed badly! The Senate votes on the fiscal package Monday at 3:00 pm. Assuming it passes, the House of Representatives is likely to vote later in the week. Congress plans to adjourn for the year December 17.
President Barack Obama’s tax-cut deal with Republicans will pass in Congress, budget leaders of both parties predicted but they disagreed on whether the plan might be altered.
Republican Paul Ryan, who becomes House Budget Committee chairman in January, and Democrat Kent Conrad, chairman of the Senate Budget Committee, said the plan will be sent to Obama’s desk though Conrad said he hoped House Democrats would change estate tax provisions he considers too generous to the wealthy.
In interviews airing this weekend on Bloomberg Television’s “Political Capital with Al Hunt,†both men said they expect Congress to pivot from tax-cutting to reducing the budget deficit early next year before a vote that will be required to raise the federal debt limit.
“There has got to be an agreement to deal with our long- term debt challenge,†Conrad said Otherwise, “extending the debt limit will not happen but for short periods of time”.
Ryan, of  Wisconsin, said he plans to lead the Republican push to cut domestic spending by $100 billion early next year, before the debt-limit vote.
“The debt ceiling obviously is going to have to be increased if we’re not going to default,†Ryan said. “So the question is, what do we get in exchange for that?â€
“We want to bring spending back to something like pre- binge, pre-spending levels of 2008. So that means we want to go after a good $100 billion,†he said.
Posted By thestatedtruth.com on December 12, 2010
Looks like we’re in a real pickle, if we try to borrow our way out of this mess, then the dollar will plunge, and if we go the austerity route-we have another World recession. Who would know better then Japan!  They say “The world is set for a long-term structural slump reminiscent of the 1870s ..The reason for the slowdown? Governments are putting fiscal austerity ahead of restoring stable growth.
This comes from Eisuke Sakakibara, Japan’s former top currency official. He is known as “Mr. Yen†for his ability to move markets. Because Tokyo’s revolving-door politics often sends a new face to each Group of 20 meeting, he is one of the few Japanese constants in market circles. Traders may not know the latest finance minister’s name, but they know Sakakibara.
Japan is the master of muddling along, decade after decade, with little growth to show for it. And Sakakibara was a key player when Japan faced everything from the Asian crisis to Russia’s default to the onset of deflation to a banking collapse that saw the demise of Yamaichi Securities Co.
So, when an economist with Sakakibara’s background says “the world is set for a long-term structural slump reminiscent of the 1870s†when average global annual growth was about 1 percent, I can’t help but listen. The reason for the slowdown? Governments are putting fiscal austerity ahead of restoring stable growth.
Yes, there’s an eye-rolling quality to a former Finance Ministry mandarin giving economic advice. After all, officials there did Japan’s 126 million people a disservice by punting reform far down the road. They just borrowed and borrowed, leaving Japan with the largest public debt among industrialized nations and no exit strategy in sight.
Yet recent data in the U.S. and Japan and financial turbulence in Europe suggest a fresh global recession is a distinct possibility in 2011. If that happens, what levers are realistically available to revive demand? Interest rates are already at, or close to, zero. That leaves increased government spending as the only real way to stabilize things.
The U.S. is starting to rattle bondholders with its borrowing binge. President Barack Obama’s stimulus isn’t working the magic economists hoped. Neither is the Federal Reserve, as it goes the way of Japan with quantitative easing.
1937 Again…..Worse, in the U.S. and other major economies, is the risk that it may be 1937 all over again. It was then that President Franklin Delano Roosevelt got stingy with stimulus, assuming that the Great Depression was over. The next year saw the economy in full retreat.
If Sakakibara is right, the global economy is in deep trouble. He envisions a broad slowdown that might drag on for seven to eight years. China can live a couple of years without U.S. and European growth, but eight?
That so many Treasuries are held in China and elsewhere makes the U.S. highly vulnerable.Â
Japan is a cautionary tale. On the surface, the 4.5 percent annualized increase in third-quarter gross domestic product looked promising. The detail, however, showed that deflation is worsening no matter how many yen the Bank of Japan churns into the economy.
This is anything but a typical recession, and world leaders are too distracted to see it.
Posted By thestatedtruth.com on December 12, 2010
 “The top 1 percent of wage earners in America earned more than the bottom 48 percent of Americans.Â
Source:Â Social Security
Substantial income inequality is not the path to a strong and vibrant middle class. 17 percent of Americans are either unemployed or underemployed so the lower end of the curve is dragging more people lower. Yet the top end remains rather strong. Some will argue that the very wealthy have also been hit. This is true and we have seen this in the top wage categories. But this is the difference between earning $50 million and $40 million. The marginal impact on lifestyle is minimal. Losing your income when you have a household making $50,000 combined and suddenly a $25,000 wage earner is gone can throw things into a tailspin.
What happens if the car breaks down? What happens if you get a cavity? What happens if you lose your job? You can see how tight the budget is above and we are keeping it basic. Many are told by financial planners to sock away 9 months of emergency funds. It will take years for the average American to put away $22,500. Is it any wonder why millions of Americans rely on Social Security as their main source of income? Millions of Americans are still on verge of losing their unemployment insurance and are basically one check away from being on the streets conjuring up visions of soup lines of the Great Depression. The average income doesn’t even come close to paving a way to a middle class lifestyle. What you have is a shrinking middle class where people are working harder and harder yet being thrown off the treadmill one by one.
More at: http://www.mybudget360.com/
Posted By thestatedtruth.com on December 12, 2010

Setup Next Week: Cold East, Mild West
Pictured to the right is the incoming large dip in the jet stream taking hold in the East behind a storm which brought blizzard conditions to the Midwest.
This will allow temperatures to fall 10 to 30 degrees below average to kick off the new week.
The opposite reaction is a bulge northward in the jet stream over the West, resulting in mild temperatures and some possible record highs.
Posted By thestatedtruth.com on December 11, 2010
Some think state secrets should be protected. It is a hot topic to say the least. The counter to that is reviewed below from the recently arrested Julian Assange.  Please note that the reviewed article below is not the indicative opinion of TheStatedTruth.com……………
Don’t Shoot Messenger For Revealing Uncomfortable Truths
By Julian Assange
Wikileaks deserves protection, not threats and attacks.
In 1958 a young Rupert Murdoch, then owner and editor of Adelaide’s The News, wrote: “In the race between secrecy and truth, it seems inevitable that truth will always win.”
His observation perhaps reflected his father Keith Murdoch’s expose that Australian troops were being needlessly sacrificed by incompetent British commanders on the shores of Gallipoli. The British tried to shut him up but Keith Murdoch would not be silenced and his efforts led to the termination of the disastrous Gallipoli campaign.
Nearly a century later, WikiLeaks is also fearlessly publishing facts that need to be made public.
I grew up in a Queensland country town where people spoke their minds bluntly. They distrusted big government as something that could be corrupted if not watched carefully. The dark days of corruption in the Queensland government before the Fitzgerald inquiry are testimony to what happens when the politicians gag the media from reporting the truth.
These things have stayed with me. WikiLeaks was created around these core values. The idea, conceived in Australia, was to use Internet technologies in new ways to report the truth.
WikiLeaks coined a new type of journalism: scientific journalism. We work with other media outlets to bring people the news, but also to prove it is true. Scientific journalism allows you to read a news story, then to click online to see the original document it is based on. That way you can judge for yourself: Is the story true? Did the journalist report it accurately?
Democratic societies need a strong media and WikiLeaks is part of that media. The media helps keep government honest. WikiLeaks has revealed some hard truths about the Iraq and Afghan wars, and broken stories about corporate corruption.
People have said I am anti-war: for the record, I am not. Sometimes nations need to go to war, and there are just wars. But there is nothing more wrong than a government lying to its people about those wars, then asking these same citizens to put their lives and their taxes on the line for those lies. If a war is justified, then tell the truth and the people will decide whether to support it.
If you have read any of the Afghan or Iraq war logs, any of the U.S. embassy cables or any of the stories about the things WikiLeaks has reported, consider how important it is for all media to be able to report these things freely.
WikiLeaks is not the only publisher of the U.S. embassy cables. Other media outlets, including Britain’s The Guardian, The New York Times, El Pais in Spain and Der Spiegel in Germany have published the same redacted cables.
Yet it is WikiLeaks, as the coordinator of these other groups, that has copped the most vicious attacks and accusations from the U.S. government and its acolytes. I have been accused of treason, even though I am an Australian, not a U.S., citizen. There have been dozens of serious calls in the US for me to be “taken out” by U..S. special forces. Sarah Palin says I should be “hunted down like Osama bin Laden”, a Republican bill sits before the US Senate seeking to have me declared a “transnational threat” and disposed of accordingly. An adviser to the Canadian Prime Minister’s office has called on national television for me to be assassinated. An American blogger has called for my 20-year-old son, here in Australia, to be kidnapped and harmed for no other reason than to get at me.
And Australians should observe with no pride the disgraceful pandering to these sentiments by Julia Gillard and her government. The powers of the Australian government appear to be fully at the disposal of the U.S. as to whether to cancel my Australian passport, or to spy on or harass WikiLeaks supporters. The Australian Attorney-General is doing everything he can to help a U.S. investigation clearly directed at framing Australian citizens and shipping them to the U.S.
Prime Minister Gillard and U.S. Secretary of State Hillary Clinton have not had a word of criticism for the other media organisations. That is because The Guardian, The New York Times and Der Spiegel are old and large, while WikiLeaks is as yet young and small.
We are the underdogs. The Gillard government is trying to shoot the messenger because it doesn’t want the truth revealed, including information about its own diplomatic and political dealings.
Has there been any response from the Australian government to the numerous public threats of violence against me and other WikiLeaks personnel? One might have thought an Australian prime minister would be defending her citizens against such things, but there have only been wholly unsubstantiated claims of illegality. The Prime Minister and especially the Attorney-General are meant to carry out their duties with dignity and above the fray. Rest assured, these two mean to save their own skins. They will not.
Every time WikiLeaks publishes the truth about abuses committed by U.S. agencies, Australian politicians chant a provably false chorus with the State Department: “You’ll risk lives! National security! You’ll endanger troops!” Then they say there is nothing of importance in what WikiLeaks publishes. It can’t be both. Which is it?
It is neither. WikiLeaks has a four-year publishing history. During that time we have changed whole governments, but not a single person, as far as anyone is aware, has been harmed. But the U.S., with Australian government connivance, has killed thousands in the past few months alone.
U.S. Secretary of Defence Robert Gates admitted in a letter to the U.S. congress that no sensitive intelligence sources or methods had been compromised by the Afghan war logs disclosure. The Pentagon stated there was no evidence the WikiLeaks reports had led to anyone being harmed in Afghanistan. NATO in Kabul told CNN it couldn’t find a single person who needed protecting. The Australian Department of Defence said the same. No Australian troops or sources have been hurt by anything we have published.
But our publications have been far from unimportant. The U.S. diplomatic cables reveal some startling facts:
In its landmark ruling in the Pentagon Papers case, the U.S. Supreme Court said, “only a free and unrestrained press can effectively expose deception in government”. The swirling storm around WikiLeaks today reinforces the need to defend the right of all media to reveal the truth.
Julian Assange, editor-in-chief of WikiLeaks.
Posted By thestatedtruth.com on December 11, 2010
What’s the old Boy Scout motto……”Be Prepared”…well it looks like we are!
On Oct. 31, the Maryland-based U.S. Cyber Command became fully operational, and its commander is also the head of the National Security Agency, the premier U.S. government entity for signals intelligence.
“USCYBERCOM plans, coordinates, integrates, synchronizes and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full spectrum military cyberspace operations in order to enable actions in all domains, ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries.”
In May 2010, General Keith Alexander, the confirmed commander of U.S. Cyber Command, outlined his views in a report for the United States House Committee on Armed Services subcommittee:
“My own view is that the only way to counteract both criminal and espionage activity online is to be proactive. If the U.S. is taking a formal approach to this, then that has to be a good thing. The Chinese are viewed as the source of a great many attacks on western infrastructure and just recently, the U.S. electrical grid. If that is determined to be an organized attack, I would want to go and take down the source of those attacks. The only problem is that the Internet, by its very nature, has no borders and if the U.S. takes on the mantle of the world’s police; that might not go down so well.”
General Alexander was promoted to General and took charge of U.S. Cyber Command in a ceremony at Fort Meade.  Maj. Gen. Suzanne M. “Zan” Vautrinot is Director of Plans and Policy, U.S. Cyber Command, and is responsible for the development and coordination of issues as related to cyberspace operations policy, doctrine, organization, capabilities and requirements.
More at: http://en.wikipedia.org/wiki/United_States_Cyber_Command
Posted By thestatedtruth.com on December 11, 2010
By Sean Noonan
A recent batch of WikiLeaks cables led Der Spiegel and The New York Times to print front-page stories on China’s cyber-espionage capabilities Dec. 4 and 5. While China’s offensive capabilities on the Internet are widely recognized, the country is discovering the other edge of the sword.
China is no doubt facing a paradox as it tries to manipulate and confront the growing capabilities of Internet users. Recent arrests of Chinese hackers and People’s Liberation Army (PLA) pronouncements suggest that China fears that its own computer experts, nationalist hackers and social media could turn against the government. While the exact cause of Beijing’s new focus on network security is unclear, it comes at a time when other countries are developing their own defenses against cyber attacks and hot topics like stuxnet and WikiLeaks are generating new concerns about Internet security.
One of the U.S. State Department cables released by WikiLeaks focuses on the Chinese-based cyber attack on Google’s servers that became public in January 2010. According to a State Department source mentioned in one of the cables, Li Changchun, the fifth highest-ranking member of the Communist Party of China (CPC) and head of the Party’s Propaganda Department, was concerned about the information he could find on himself through Google’s search engine. He also reportedly ordered the attack on Google. This is single-source information, and since the cables WikiLeaks released do not include the U.S. intelligence community’s actual analysis of the source, we cannot vouch for its accuracy. What it does appear to verify, however, is that Beijing is regularly debating the opportunities and threats presented by the Internet.
On Nov. 2, the People’s Liberation Army Daily, the official paper for the PLA and the primary medium for announcing top-down policy, recommended the PLA better prepare itself for cyber threats, calling for new strategies to reduce Internet threats that are developing “at an unprecedented rate.†While the report did not detail any strategies, it quoted a PLA order issued for computer experts to focus on the issue.
The Nov. 2 PLA announcement is part of a long trend of growing network-security concerns in China. In 2009, Minister of Public Security Meng Jianzhu emphasized that the development of the Internet in China created “unprecedented challenges†in “social control and stability maintenance.†In June 2010, the State Council Information Office published a white paper on the growing threat of cyber crime and how to combat it. Clearly, these challenges have been addressed this year. The Ministry of Public Security (MPS) announced Nov. 30 that it had arrested 460 suspected hackers thought to have been involved in 180 cases so far in 2010. This is part of the MPS’ usual end-of-year announcement of statistics to promote its success. But the MPS announcement also said that cyber crime had increased 80 percent this year and seemed to blame the attacks only on hackers inside China.
These were cases mainly of producing and selling “Trojan†programs (malware that looks legitimate), organizing botnets, assisting others in carrying out denial-of-service attacks and invading government websites. The MPS also closed more than 100 websites that provided hackers with attack programs and taught them various tactics.
The PLA already has two notoriously large and capable network security units: the Seventh Bureau of the Military Intelligence Department (MID) and the Third Department of the PLA. In simple terms, the MID’s Seventh Bureau is an offensive unit, responsible for managing research institutes that develop new hacking methods, train hackers and produce new hardware and software. The PLA Third Department, defensive in nature, is the third largest signals intelligence-monitoring organization in the world. STRATFOR sources with expertise in network security believe that China’s government-sponsored hacking capabilities are the best in the world. But this perception is based in part on the fact that China demonstrates these capabilities quite often. The United States, on the other hand, is much more restrained in exercising its offensive cyber capabilities and is not inclined to do so until there is a dire and immediate need, such as war.
The details of China’s escalating effort to improve network security are still murky, but one recently announced campaign against software piracy is notable. On Nov. 30, Deputy Commerce Minister Jiang Zengwei announced a new six-month crackdown on illegally copied products in China. He said the focus was on pirated software, counterfeit pharmaceuticals and mislabeled agricultural products. The Chinese public has pushed for more regulation of pharmaceuticals and food due to a rising number of cases in which people have become sick or even died because of falsely labeled or tainted products, such as melamine-contaminated milk. But Beijing seems to be even more concerned about the vulnerabilities created by running unlicensed and non-updated software, and publicizing the crackdown is clearly an attempt by Beijing to appease Western governments and businesses that are placing growing pressure on China.
Indeed, China has a sizable counterfeit economy, much to the ire of Western businesses. While Beijing may placate Westerners by announcing crackdowns for the benefit of international audiences, it takes more forceful measures when it sees a larger threat to itself, and the security emphasis now seems to be on the threat of running insecure software on government computers. The problem with unlicensed software is that it does not receive automatic updates from the manufacturer, which usually are sent out to fix vulnerabilities to malware. Unlicensed software is thus left open to viral infiltration. It is also cheap and easy to get, which makes it pervasive throughout both government and private computer networks.
One of the measures Beijing has started to implement is requiring licensed software to be installed on new computers before they are sold, which also gives the government an opportunity to install censorship measures like Green Dam. One persistent problem is that much of the pre-installed software still consists of pirated copies. While China has released statistics showing that the use of legitimate software in China has increased dramatically, the Business Software Alliance, an international software industry group, estimates that 79 percent of the software sold in China in 2009 was illegally copied, creating a loss to the industry of $7.6 billion in revenue. Even more important to Beijing, these statistics mean the vast majority of Chinese computer systems — government and private alike — remain vulnerable to malware.
At the same Nov. 30 news conference at which Jiang announced the new anti-piracy initiative, Yan Xiaohong, deputy head of the General Administration of Press and Publication and vice director of the National Copyright Administration, announced a nationwide inspection of local and central government computers to make sure they were running licensed software. While this suggests Beijing’s major concern is the security of government computers, it also emphasizes how widespread the unlicensed software problem is.
This new focus on using legitimate software, however, will not be a complete solution to China’s Internet vulnerabilities. There has been little effort to stop the selling of copied software, and it is still very easy to download other programs, licensed and unlicensed, and malware along with them (such as QQ). Moreover, the new security measures are dealing only with the symptoms, not the underlying problem, of a counterfeit-heavy economy. A six-month crackdown will not undermine or eliminate software piracy in China; to do so would require an immense and sustained investment of time, money and manpower. Indeed, China has been a hub for pirating software, films and other copyrighted material for so long that the enormous domestic economic base that has grown up around it would be virtually impossible to dismantle. In any case, vulnerabilities still exist in legitimate software, even if it is better protected against novice hackers. New vulnerabilities are constantly being found and exploited until software companies come up with the appropriate patches.
China’s highly developed hacking capabilities, more offensive than defensive, include Internet censorship measures like the infamous Great Firewall, and the official police force run by the MPS specifically to monitor Chinese Internet traffic and censor websites is 40,000 strong. China also has developed two unofficial methods of censorship. First, operators of private websites and forums must follow certain government regulations to prevent statements critical of the government from being disseminated, which encourages private operators to be their own censors. Second, there is a veritable army of nationalistic computer users in China that include “hacktivist†groups such as the Red Hacker Alliance, China Union Eagle and the Honker Union, with thousands of members each. They became famous after the 1999 “accidental†bombing of the Chinese Embassy in Belgrade, which prompted China-based hackers to attack and deface U.S. government websites. The Chinese government, state-owned enterprises and private companies also engage public relations firms to hire, deploy and manage what have become colloquially known as “Party of Five Maoists.†These are individuals who get paid half a yuan (5 mao) for every positive Internet post they write regarding government policy, product reviews and other issues.
But as China’s Internet-using population nears 400 million, with nearly 160 million using social networking, Beijing recognizes the risk of all this spiraling out of control. Censors have not been able to keep up on the social-networking front. Even with limited or banned access to sites like Twitter and Facebook, their Chinese versions, Weibo and Kaixin, for example, are expanding exponentially. While the government may exercise more control over the Chinese-based sites, it cannot keep up with the huge number of posts on topics the CPC considers disharmonious. The recent announcement of Liu Xiaobo’s Nobel Peace Prize is an example of news that was not reported at first in Chinese media but through social networking sites, spreading like wildfire. And the censorship is not exclusive; even non-dissidents can be censored, such as Prime Minister Wen Jiabao when he recently called for limited political reform.
China’s large Internet population will not all be nationalists. And if those who learn skills from informal hackers turn into dissidents, Beijing would consider them a serious threat. The Internet presents exactly the type of tool that could pose a major threat to the CPC because it spans regions, classes and ethnicities. Most social grievances are local and economic or ethnic-based. The potential for one opposition group to be united nationwide over the Internet is one of Beijing’s gravest concerns. It has realized that a weapon it once wielded so deftly against foreign powers and business entities can now be used against Beijing.
At the same time Beijing reached this realization, WikiLeaks demonstrated the possibility for sensitive government information to be spread globally through the Internet. Beijing saw that if the United States, with its expertise in signals intelligence and security, could be vulnerable to such a threat, so could China. Stuxnet demonstrated the vulnerability of important infrastructure to cyber attack, one reason for China’s new emphasis on licensed software (Iran is known to run unlicensed Siemens software). China’s recent emphasis on network security is likely linked to all of these factors, or it may be due to a threat seen but as yet unpublicized, such as a cyber attack or leak inside China that the government has been able to keep quiet.
Other countries have also been implementing new network security measures, most notably the United States. On Oct. 31, the Maryland-based U.S. Cyber Command became fully operational, and its commander is also the head of the National Security Agency, the premier U.S. government entity for signals intelligence. (Thus, China’s giving Internet security responsibility to the PLA should come as no surprise to the United States.) And as China realizes the difficulties of defending against attacks in cyberspace, which tend to favor the offense, the United States is wrestling with the same problems and complexities as it tries to shield government, civilian and commercial computer systems, all of which require different degrees of control and operate under different laws. As cyber espionage and cyber sabotage become even greater concerns, China will be forced to face the far more difficult task of not only pecking away at the Pentagon’s firewalls but also providing for its own internal system security.
These new efforts all contradict China’s long-standing policy of cultivating a population of nationalistic computer users. This effort has been useful to Beijing when it sees a need to cause disruption, whether by attacking U.S. sites after perceived affronts like the Chinese Embassy bombing in Belgrade or preventing access from powerful foreign entities like Google. But China has also recognized that developing these public capabilities can be dangerous. Nationalist Chinese hackers, if motivated by the right cause and united through the pervasive Internet, can always turn on the government. And the situation seems to have more and more governments on edge, where simple mistakes can raise suspicions. China’s redirection of a large amount of Internet traffic in April caused an outcry from the United States and other countries, though it may well have been an accident.
It is hard to tell what Beijing sees, specifically, as a first-tier cyber threat, but its decision to develop an effective response to all manner of threats is evident.
.
Reprinting or republication of this report on websites is authorized by prominently displaying the following sentence, including the hyperlink to STRATFOR, at the beginning or end of the report.Simply copy and paste this code:
“China and its Double-edged Cyber-sword is republished with permission of STRATFOR.”
Posted By thestatedtruth.com on December 10, 2010
According to research released today by Cogent, affluent Americans are closing brokerage accounts an increasing clip: 13% of affluent individuals closed at least one account in the last 12 months, more than twice the pace of account closures in the previous five years.
Fidelity Investments:Â Â Â Â Â Â Â Â Â Â 15%
Wells Fargo Advisors:Â Â Â Â Â Â Â Â 11%
Merrill Lynch:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 10%
E*Trade:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 10%
Morgan Stanley  SB:             8%
TD Ameritrade:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 8%
Charles Schwab:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 7%
Ameriprise:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 6%
Vanguard:Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â Â 6%
Posted By thestatedtruth.com on December 10, 2010
Economic Inequality…..we present a great 3 minute summary, which even a third or fourth grader will understand.   What is gradually becoming accepted as the most troubling social, economic and political development in America, namely a record amount of income,wealth and social inequality.
From the CBS 60 Minute interview of Fed Chairman Ben Bernanke:
Q: The gap between rich and poor in this country has never been greater. In fact, we have the biggest income disparity gap of any industrialized country in the world. And I wonder where you think that’s taking America.
A: Well, it’s a very bad development. It’s creating two societies. And it’s based very much, I think, on– on educational differences the unemployment rate we’ve been talking about. If you’re a college graduate, unemployment is five percent. If you’re a high school graduate, it’s ten percent or more. It’s a very big difference. It leads to an unequal society and a society– which doesn’t have the cohesion that…that we’d like to see.
Must Watch Vidio… Eonomic Inequity in the United States, watch this on youtube at…………………. http://www.youtube.com/watch?feature=player_detailpage&v=vMdbS1VU5do
Posted By thestatedtruth.com on December 10, 2010
Thursday, as negotiators from nearly 200 countries met in Cancun to strategize ways to keep the planet from getting hotter, the temperature in the seaside Mexican city plunged to a 100-year record low of 54° F.
Posted By thestatedtruth.com on December 10, 2010
Posted By thestatedtruth.com on December 10, 2010
For those who understand this, no explanation is needed.Â
For those who do not understand this, no explanation is possible, you flunked kindergarten.
Kindergarten Economics….The Tax System Explained In Layman Terms
Ten men go out for beer and the bill for all ten comes to $100…If they paid their bill the way we pay our taxes, it would go something like this.Â
Â
The first four men (the poorest) would pay nothing.Â
Â
The fifth would pay $1.Â
Â
The sixth would pay $3.Â
The seventh would pay $7.
The eighth would pay $12.Â
The ninth would pay $18.Â
Â
The tenth man (the richest) would pay $59.Â
So, that’s what they decided to do.Â
Â
The ten men drank in the bar every day and seemed quite happy with the arrangement, until one day, the owner threw them a curve ball. “Since you are all such good customers,” he said, “I’m going to reduce the cost of your daily beer by $20.” Drinks for the ten men would now cost just $80.Â
The group still wanted to pay their bill the way we pay our taxes. So the first four men were unaffected.  They would still drink for free. But what about the other six men? The paying customers? How could they divide the $20 windfall so that everyone would get his fair share? They realized that $20 divided by six is $3.33. But if they subtracted that from everybody’s share, then the fifth man and the sixth man would each end up being paid to drink his beer. So, the bar owner suggested that it would be fair to reduce each man’s bill by a higher percentage.Â
They decided to follow the principle of the tax system they had been using, and he proceeded to work out the amounts he suggested that each should now pay.Â
And so the fifth man, like the first four, now paid nothing (100% saving).Â
Â
The sixth now paid $2Â instead of $3 (33% saving).Â
The seventh now paid $5Â instead of $7 (28% saving).Â
The eighth now paid $9Â instead of $12 (25% saving).Â
Â
The ninth now paid $14Â instead of $18 (22% saving).Â
Â
The tenth now paid $49Â instead of $59 (16% saving).Â
Â
Each of the six were better off than before. And the first four plus the fifth continued to drink for free. But, once outside the bar, the men began to compare their savings.
“I only got a dollar out of the $20 saving,” declared the sixth man. He pointed to the tenth man, “but he got $10!”Â
“Yeah, that’s right, “exclaimed the fifth man. “I only saved a dollar too.  It’s unfair that he got ten times more benefit than me!” “That’s true!” shouted the seventh man. “Why should he get $10 back, when I got only $2?   The wealthy get all the breaks!” “Wait a minute, “yelled the first four men in unison, “we didn’t get anything at all. This new tax system exploits the poor!”Â
The nine men surrounded the tenth and beat him up.Â
Â
The next night the tenth man didn’t show up for drinks, so the nine sat down and had their beers without him.  But when it came time to pay the bill, they discovered something important. They have only enough money $51 between all of them to pay for about half of the bill! Â
And this message is directed at our dumb self serving elected officials, naieve journalists and government powers to be.  Tax the rich but don’t make it so bad that they leave.
The people who already pay the highest taxes will naturally get the    most benefit from a tax reduction. Tax them too much, attack them for being wealthy, and they just may not show up anymore.  In fact, they might start drinking overseas, where the atmosphere is somewhat friendlier.Â
     www.theststedtruth.com
Posted By thestatedtruth.com on December 9, 2010
The monster snowstorm slated for this weekend will hit portions of the Midwest, eastern Great Lakes, central Appalachians, Ontario and Quebec hardest.
The heaviest snow is most likely to begin over Iowa and surrounding areas Saturday. The snow will then encompass Michigan, western New York, southern and southwestern Ontario and southwestern and central Quebec for the remainder of the weekend.

Places like Corry, Pennsylvania have received over 3 feet of snow from the recent lake effect. The coming storm and the lake effect that follows will push snowfall totals to incredible levels.
The dynamics of this event are such that two storm centers are likely. One storm center will first track northeastward into the lower Great Lakes and weaken. Next, a new storm center will form over eastern areas of the mid-Atlantic and track northward through the Hudson Valley of New York into eastern Quebec. Areas near east and south of the tracks of both storms will get a wintry mix of snow, sleet and rain, or even plain rain. The rain scenario is expected across the Ohio Valley, the I-95 mid-Atlantic, and essentially all of New England, New Brunswick and Nova Scotia.
At some point over the central Appalachians, the changeover to a mix or rain will stop as the mid-Atlantic storm takes over and causes temperatures to plummet, prolonging snow farther north.
More at:http://www.accuweather.com/blogs/news/story/42704/monster-storm-could-be-winters.asp
Posted By thestatedtruth.com on December 9, 2010
Europe and Russia are looking at a super cold winter ….we’ve warned about this for a while! Sun spots have been indicating more bad weather dead ahead! When this winter is all said and done we may see 500 year old records fall.
Britain has the coldest 1st-8th December on (CET) record, with monthly records starting in 1659. The daily data started in 1772.” So….it appears that we can only confirm this was the coldest since 1772.
And…In FranceÂ
Paris city authorities asked residents to avoid using their cars after the heaviest snowfall in nearly a quarter of a century covered city streets with ice and slush, causing traffic jams that prevented commuters getting home on Wednesday night. “Stuck”, read a headline in the popular daily Le Parisien, while Le Figaro heralded “The great freezing of Paris”.
Posted By thestatedtruth.com on December 9, 2010
The Federal Reserves’s worst nightmare has just come true.
Representative Ron Paul, Texas Republican and author of “End the Fed,†will take control of the House subcommittee that oversees the Federal Reserve.
House Financial Services chairman-elect Spencer Bachus, an Alabama Republican, selected Paul, 75, to lead the panel’s domestic monetary policy subcommittee when their party takes the House majority next month.
“This is the leadership team that crafted the first comprehensive financial reform bill to put an end to the bailouts, wind down the taxpayer funding of Fannie Mae and Freddie Mac, and enforce a strong audit of the Federal Reserve,†Bachus said in a statement.
Paul said in an interview last week he plans a slate of hearings on U.S. monetary policy and will restart his push for a full audit of the Fed’s functions.
“We are ready to hit the ground running, and I look forward to continuing our work in the next Congress,†Bachus said.
Copyright © 2025 The Stated Truth